- Current Affairs
- China
- North Korea
- Active Measures-Hybrid Warfare
- Cyberwarfare
- Infrasonic Weapons
- Russian Agenda
- Yandex-User data illicitly shared with Russian Intelligence
Wikileaks- Julian Assange released classified information and damaging emails
- Big Data
- Yandex-Charged with Treason in Ukraine for stealing user data and giving to Russian Intelligence
- Kaspersky Labs- Russian antivirus company plants malware/spyware
- Psy-Group -Joel Zamel‘s Israeli Intelligence Psyops
- George Nader Lebanese Putin liaison paid Zamel $2m after election, set August 3, 2016 meeting and several between Trump Campaign, UAE, and Saudi Arabia Cooperating Witness; Pedophile
- Newt Gingrich–Zamel told the former House Speaker, to offer PSY Group services to Jared Kushner
- Cambridge Analytica-British– Trump Campaign & Brexit
- SCL Elections/Emerdata-parent co. of Cambridge Analytica Global campaigns and black ops using
- i360-Koch Brothers’ American data
- Pioneer Solutions
- Big Data Dolphins
- Data Trust
- AggregateIQ
- Voting Machine Issues– Votes Flipping, etc.
- Right Wing Media
- 2016 Social Media Campaign
- Bernie Sanders
- The Alt-Right
LinkedIn, Dropbox, Formspring (Anthony Weiner’s sexting),voter registration-themed spear-phishing campaign, the DNC Hack 2016
China Has Abandoned a Cybersecurity Truce With the U.S., Report Says Bloomberg By Alyza Sebenius
2016 Presidential Campaign Hacking Fast Facts CNN
It’s become clear that Putin intends to sway elections in the Western world. The US, France and UK have been hacked and the US election was influenced by the combined efforts of hackers, American voices of the Alt-Right and the trolls from the US and abroad. Actual interference into voter rolls and machine vote tallies is being investigated…but not by the agency designed to investigate. Trump’s shutting that down…and instead suggesting a Cyber Security Taskforce with Putin himself at the G20 summit. Many speculate that Putin’s trying to win the war without firing a bullet, so to speak… taking over one free country at a time and encouraging authoritarian, far-right regimes which restrict women’s rights and freedoms of all kinds.
- TEA PAIN on Spectrum Health’s Role in the Trump-Russia Server Scandal
- TEA PAIN on Debunking Trump Tower’s Alfa Bank Server Scandal “Explanation”
- TEA PAIN on Data Patterns Reveal Trump Tower/Spectrum Health Ran a “Stealth Data Machine” With Russia. We pull back the curtain on Jared Kushner’s “Stealth Data Machine.”
- TEA PAIN on New Analysis Supports Database Replication Theory Between Trump Tower and Alfa Bank
- TEA PAIN on WikiLeaks Moves Two Servers to Russia
Here’s exactly how Russia can hack the 2018 elections Vice News July 10, 2017
Spearfishing — Russia’s attempt to hack US election officials, explained Vox
Foreign governments hacking US elections is a real threat. We need to be ready. “According to the NSA, the Russian government began its hacking efforts by attempting to infiltrate an American election technology vendor that the Intercept says is a Florida-based company called VR Systems. The attackers used a “spear phishing” technique, sending personalized emails to several employees of the company to try to trick the employees into entering their passwords into a fake Google login form. Next, the attackers posed as employees of the voting technology company to attack election officials in jurisdictions that used the company’s products. Using real documentation stolen from VR Systems, the hackers created malicious Microsoft Word documents that compromise a victim’s computer when they are opened. The documentation was for EVid, software that manages the voter checkin process at a polling place. We don’t know how many of those 122 election officials clicked on the malicious link and had their computers compromised. We don’t know if Russian spies did anything malicious once they gained access. The attackers sent out malicious emails to 122 election officials around the country” —Vox News
DNC HACK Spring 2016
February 16, 2018: Mueller Issues indictment against 13 Russian Nationals with working for the Russian Internet Research Agency to foment discord in the US. CNN These people impersonated Americans and held rallies for and against Trump issues, resulting in the count for Identity Theft.
Timeline:
June 14, 2016 – The Washington Post reports hackers working for the Russian government accessed the Democratic National Committee’s computer system, stealing oppositional research on Donald Trump and viewing staffers’ emails and chat exchanges. The Kremlin, however, denies that the government was linked to the hack, and a US official tells CNN that investigators have not yet concluded that the cyberattack was directed by the Russian government.
- June 15, 2016 – A cybersecurity firm hired by the DNC posts a public notice on its website describing an attack on the political committee’s computer network by two groups associated with Russian intelligence. According to the post, two Russian-backed groups called “Cozy Bear” and “Fancy Bear” tunneled into the committee’s computer system. In response, a blogger called Guccifer 2.0 claims that he alone conducted the hack, not the Russians. As proof, he posts internal DNC memos and opposition research on Trump. Furthermore, Guccifer 2.0 claims to have passed along thousands of files to WikiLeaks. Trump offers his own theory on the origins of the attack: suggesting in a statement that the DNC hacked itself to distract from Hillary Clinton’s email scandal.
- July 22, 2016 – Days before the Democratic National Convention, WikiLeaks posts nearly 20,000 emails hacked from the DNC server. The documents include notes in which DNC chair Debbie Wasserman Schultz insults staffers from the Bernie Sanders campaign and messages that suggest the organization was favoring Clinton rather than remaining neutral. Wasserman Schultz resigns in the aftermath of the leak.
- July 25, 2016 – The FBI announces it has launched an investigation into the DNC hack. Although the statement doesn’t indicate that the agency has a particular suspect or suspects in mind, US officials tell CNN they think the cyberattack is linked to Russia.
- July 27, 2016 – During a press conference, Trump declares Russia may have hacked the State Department. He connects the suspected Russian cyberattack on the DNC to Clinton’s use of a private email server while she was Secretary of State. “Russia, if you’re listening, I hope you’re able to find the 30,000 emails that are missing,” says Trump. Newt Gingrich, a Trump surrogate, defends Trump in a Tweet, dismissing the comment as a “joke.”
- August 12, 2016 – Hackers publish cell phone numbers and personal email addresses for Nancy Pelosi and other members of the Democratic Congressional Campaign Committee. Pelosi says she has received “obscene and sick calls” from strangers. She advises targeted colleagues not to allow children or family members to answer the phone or read text messages.
- September 1, 2016 – During an interview with Bloomberg News, President Vladimir Putin says that he and the Russian government have no ties to the hackers. He says that the identity of the culprit or culprits is not as important as the content of the leaks, and ultimately the hackers revealed important information for voters.
- September 22, 2016 – Democrats Dianne Feinstein and Adam Schiff, ranking members of the Senate and House Intelligence Committees, issue a joint statement declaring that based on information they received during congressional briefings, they believe that Russian intelligence agencies are carrying out a plan to interfere with the election. They call on Putin to order a halt to the activities.
- September 26, 2016 – During a presidential debate with Clinton, Trump questions whether the DNC cyberattack was carried out by a state-sponsored group or a lone hacker. “It could be Russia, but it could also be China. It could also be lots of other people. It also could be somebody sitting on their bed that weighs 400 pounds.”
- October-November 2016 – Over the course of a month, WikiLeaks publishes more than 58,000 messages hacked from the account of John Podesta, Clinton’s campaign chairman.
- October 6, 2016 – DCLeaks, a self-described collective of “hacktivists” seeking to expose the influence of special interests on elected officials, publishes a batch of documents stolen from Clinton ally Capricia Marshall.
- October 7, 2016 – The Department of Homeland Security and the Office of National Intelligence on Election Security issues a statement declaring that the intelligence community is “confident that the Russian Government directed the recent compromises of emails from US persons and institutions.” According to the statement, document releases on websites WikiLeaks and DC Leaks mirror the methods and motivations of past Russian-directed cyberattacks.
- November 29, 2016 – A group of Democratic senators sends a letter to President Barack Obama calling on intelligence agencies to declassify information about “the Russian Government and the US election.” Sources later tell CNN that new intelligence has been shared with lawmakers suggesting that Russia’s purpose for meddling in the election was to sway voters towards Trump, rather than broadly undermining confidence in the system.
- December 9, 2016 – The Washington Post reports the CIA has determined that Russian hacking was conducted to boost Trump and hurt Clinton during the presidential campaign. The Trump transition team dismisses the CIA’s findings, releasing a statement, “These are the same people that said Saddam Hussein had weapons of mass destruction.” President Obama asks intelligence agencies to review the hacking incidents in 2016 and other cyberattacks on political campaigns dating back to 2008. The agencies are asked to deliver their findings before Obama leaves office on January 20. A Russian foreign ministry spokesman expresses skepticism about the review and asks US investigators to share their evidence of government-sponsored cyber espionage. Meanwhile, media critics question the Post’s reliance on anonymous sources for the CIA report and advise readers to be wary of claims in the article due to the lack of publicly available evidence to support the spy agency’s conclusions.
- December 10, 2016 – John McCain, Chuck Schumer, Lindsey Graham and Jack Reed issue a joint statement calling on Congressional Republicans and Democrats to work cooperatively on securing future elections and stopping cyber attacks.
- December 11, 2016 – Sources tell CNN that although US intelligence agencies share the belief that Russia played a role in the computer hacks, there is disagreement between the CIA and the FBI about the intent of the meddling. While the CIA assessment shows that the Russians may have sought to damage Clinton and help Trump, the FBI has yet to find proof that the attacks were orchestrated to elect the Republican candidate, according to unnamed officials. Furthermore, some sources say the hackers also infiltrated the Republican National Committee’s computers.
- December 12, 2016 – CNN reports that Russian hackers accessed computer accounts of Republican lawmakers and GOP organizations. A source with knowledge of the investigation says that even though hackers breached the GOP computers, they opted not to release documents en masse.
- December 13, 2016 – The New York Times publishes a detailed account of the DNC’s delayed response to initial warnings in September of 2015 that its network had been infiltrated by hackers. The report outlines how phishing emails and communication failures led to a sweeping cyberattack. The story also lays out evidence that Guccifer 2.0 and DCLeaks were linked to Russia. A second article in the Times chronicles the hacking of Democratic Congressional Campaign Committee, housed in the same building as the DNC. According to the report, Guccifer 2.0 stole tens of thousands of documents and offered them to reporters in districts where Democratic candidates were engaged in competitive races for House seats.
- December 29, 2016 – President Obama issues an executive order with sanctions against Russia. The order names six Russian individuals who allegedly took part in the presidential campaign hacking. Additionally, 35 Russian diplomats are ordered to leave the US within 72 hours.
- January 3, 2017 – Julian Assange of WikiLeaks says that the Russian government did not provide him with the hacked DNC emails during an interview with Sean Hannity on the Fox News Channel.
- January 3-4, 2017 – In a series of tweets, Trump questions the US intelligence community’s claims that the Russian government interfered with the election. He alleges that intelligence officials have delayed a scheduled meeting with him but sources tell CNN that there has been no change to the schedule. Trump also cites Assange’s interview to back his assertion that a rogue hacker, not the Russian government, may have meddled in the election.
- January 5-6, 2017 – Intelligence officials meet separately with Obama and Trump to present the results of their probe into cyber espionage during the presidential campaign. After the president and the president-elect are briefed, the Office of the Director of National Intelligence releases a declassified version of the report. According to the report, hackers did not breach voting machines or computers that tallied election results but Russians meddled in other ways. Among the findings: Putin ordered a multifaceted influence campaign that included hacking and pro-Trump propaganda; bracing for a possible Clinton win, Russian bloggers were prepared to spread a hashtag #DemocracyRIP on Election Night; paid social media users, aka “trolls,” shared stories about Clinton controversies to create a cloud of scandal around her campaign.
- January 6-7, 2017 – Trump issues a statement after his meeting with intelligence officials. In the statement, he acknowledges that the Russian government may have been linked to the DNC hacking but declares that cyberattacks did not impact the outcome of the election because voting machines were not breached. In a series of tweets, he repeats that hacking did not affect election results and says that he wants to improve relations with Russia.
- February 9, 2017 – The Washington Post reports that Trump’s national security adviser, Michael Flynn discussed sanctions with Russian ambassador Sergey Kislyak during the presidential transition. Vice President Mike Pence and other Trump administration officials said in January that Flynn did not talk about policy when he spoke to the ambassador. The Washington Post story is based on interviews with nine officials who spoke on the condition of anonymity. One day after the report is published, Trump tells reporters that he has not read the story and says he will look into it.
- February 13, 2017 – Flynn resigns. In his resignation letter, he explains that, “because of the fast pace of events, I inadvertently briefed the Vice President Elect and others with incomplete information regarding my phone calls with the Russian ambassador.”
- February 17, 2017 – Members of the Senate Intelligence Committee meet with FBI Director James Comey in a closed-door session. One attendee tells CNN that Russia was the topic of the briefing and after the meeting, committee member Marco Rubio says in a tweet that the Senate will conduct a bipartisan investigation into alleged meddling by Putin.
- March 10, 2017 – In an interview with the Washington Times, Trump ally Roger Stone says that he had limited interactions via Twitter with Guccifer 2.0 during the campaign. He says the exchanges were “completely innocuous.” The following day, the New York Times publishes its own interview with Stone, in which he says that his communication with Guccifer 2.0 took place after the DNC hack, proving there was no collusion with the Trump campaign to arrange the cyber attack.
- March 20, 2017 – During a hearing on Capitol Hill, Comey confirms that the FBI is investigating links between Russia and members of the Trump campaign.
- May 9, 2017 – President Trump fires Comey days after the FBI director testified before the Senate Judiciary Committee.
- June 1, 2017 – In public remarks, Putin says that hacking during the presidential election campaign may have been carried out by patriotic Russian citizens who felt compelled to respond to perceived slights against Russia from America. Putin says, however, that the Russian government played no role in the cyber attacks. During an interview days later, Putin says that a child could have easily hacked the American presidential campaign.
- June 5, 2017 – An investigative website, the Intercept posts a report that the Russian government coordinated a spear-phishing attack on computers at an American voting machine company and compromised at least one email account. The article is based on an NSA memo that was leaked to the Intercept. Hours after the story is published, the source of the leak is identified as a government contractor named Reality Leigh Winner, 25. She is charged with transmitting classified information.
- June 19, 2017: UpGuard revealed from June 1 to June 14, 2017 Read the Report, Data of nearly all registered US voters left unsecured for weeks in RNC trove Personal data, including names, addresses, voter registration details and social media posts, made vulnerable because of improper security settings The Guardian personal details of nearly every registered voter in the US
- June 21, 2017 – During a Senate hearing, a Department of Homeland Security official says that hackers linked to the Russian government targeted voting systems in up to 21 states.”
-
July 12, 2017 Cyber Berkut started publishing emails starting a rumor that was played on Fox News for the next 5 days. It is believed to be an alter ego of Fancy Bear, pro-Russian hacker group Rachel Maddow Show
Track what the Russian Bots are doing in Real Time here!
Steele Dossier
Quoting the Steele Dossier about planting malware in cheap Russian IT games: “In terms of the FSB’s recruitment of capable cyber operatives to carry out its, ideally deniable, offensive cyber operations, a Russian IT specialist with direct knowledge reported in June 2016 that this was often done using coercion and blackmail. In terms of ‘foreign’ agents, the FSB was approaching US citizens of Russian (Jewish) origin on business trips to Russia. In one case a US citizen of Russian ethnicity had been visiting Moscow to attract investors in his new information technology program.
The FSB clearly knew this and had offered to provide seed capital to this person in return for them being able to access and modify his IP, with a view to targeting priority foreign targets by planting a Trojan virus in the software. The US visitor was told this was common practice. The FSB also had implied significant operational success as a result of installing cheap Russian IT games containing their own malware unwittingly by targets on their PCs and other platforms.
In a more advanced and successful FSB operation, an IT operator inside a leading Russian SOE, who previously had been employed on conventional (defensive) IT work there, had been under instruction for the last year to conduct an offensive cyber operation against a foreign director of the company. Although the latter was apparently an infrequent visitor to Russia, the FSB now successfully had penetrated his personal IT and through this had managed to access various important institutions in the West through the back door.
6. The senior Russian government figure cited above also reported that non-state sponsored cyber crime was becoming an increasing problem inside Russia for the government and authorities there. The Central Bank of Russia claimed that in 2015 alone there had been more than 20 attempts at serious cyber embezzlement of money from corresponding accounts held there, comprising several billions Roubles. More generally, s/he understood there were circa 15 major organised crime groups in the country involved in cyber crime, all of which continued to operate largely outside state and FSB control. These included the so-called ‘Anunak’, ‘Buktrap‘ and ‘Metel’ organisations.
– Further evidence of extensive conspiracy between campaign team and Kremlin, sanctioned at highest levels and involving Russian diplomatic staff based in the US
– TRUMP associate admits Kremlin behind recent appearance of DNC e-mails on WikiLeaks, as means of maintaining plausible deniability
– Agreed exchange of information established in both directions.
Team using moles within DNC and hackers in the US as well as outside in Russia. PUTIN motivated by fear and hatred of Hillary CLINTON. Russians receiving intel from team on Russian oligarchs and their families in US
– Mechanism for transmitting this intelligence involves ‘pension’ disbursements to Russian emigres living in US as cover, using consular officials in New York, DC and Miami
– Suggestion from source close to TRUMP and MANAFORT that Republican campaign team happy to have Russia as media bogeyman to mask more extensive corrupt business ties to China and other emerging countries”
Top-Secret NSA Report Details Russian Hacking Effort Days Before 2016 Election June 5, 2017 The Intercept: “Russian General Staff Main Intelligence Directorate actors … executed cyber espionage operations against a named U.S. company in August 2016, evidently to obtain information on elections-related software and hardware solutions. … The actors likely used data obtained from that operation to … launch a voter registration-themed spear-phishing campaign targeting U.S. local government organizations.”
Federal contractor Reality Leigh Winner arrested for sending classified NSA intelligence to news outlet “A 25-year-old federal contractor is facing charges she leaked a classified National Security Agency document to a news outlet in May.The charges against Reality Leigh Winner came about an hour after the publication of a story based on an NSA document detailing Russian attempts to hack American voting systems in 2016.” Washington Examiner
* * *
Tea Leaves and his colleagues plotted the data from the logs on a timeline. What it illustrated was suggestive: The conversation between the Trump and Alfa servers appeared to follow the contours of political happenings in the United States. “At election-related moments, the traffic peaked,” according to Camp. There were considerably more DNS lookups, for instance, during the two conventions.
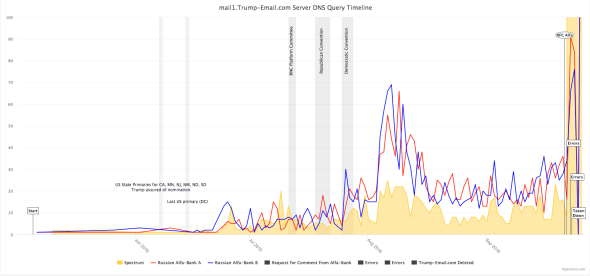
In September, the scientists tried to get the public to pay attention to their data. One of them posted a link to the logs in a Reddit thread. Around the same time, the New York Times’ Eric Lichtblau and Steven Lee Myers began chasing the story.* (They are still pursuing it.) Lichtblau met with a Washington representative of Alfa Bank on Sept. 21, and the bank denied having any connection to Trump. (Lichtblau told me that Times policy prevents him from commenting on his reporting.) Slate
The spike in August was at the same time the Mercer camp and their SuperPac money publicly joined Trump, with Kellyanne Conway replacing Paul Manafort as Campaign Director and Steve Bannon getting more heavily involved in the Campaign.
4/3/17 Keith Olberman on Trump’s panic over the Russian election hack, which may be about Cambridge Analytica getting the official voter information rolls from about 20 States. Cambridge Analytica has been run by Steve Bannon and owned by Trump’s savior donors, Robert and Rebekah Mercer. Mikhael Kalugin identified as the Steele Dossier Russian spy under surveillance at the US Embassy, and the key player in the election scheme, suddenly pulled back to Moscow.
Trump gave a speech in New York City on June 22, which was written to be delivered on June 9, the same day as the Campaign was anticipating receiving Kompromat, or a Blackmail File, on Clinton’s campaign. The press conference was delayed until the 22nd because of the Pulse nightclub shooting in Orlando. The same day as this speech was delivered, the Trump Tower – Alfa Bank Pings began. Full Transcript and Video on Politico. “Because it’s not just the political system that’s rigged. It’s the whole economy. It’s rigged by big donors who want to keep down wages. It’s rigged by big businesses who want to leave our country, fire our workers, and sell their products back into the U.S. with absolutely no consequences for them. It’s rigged by bureaucrats who are trapping kids in failing schools. It’s rigged against you, the American people. Hillary Clinton has perfected the politics of personal profit and theft. She ran the State Department like her own personal hedge fund – doing favors for oppressive regimes, and many others, in exchange for cash. Then there are the 33,000 emails she deleted. While we may not know what is in those deleted emails, our enemies probably do. So they probably now have a blackmail file over someone who wants to be President of the United States. This fact alone disqualifies her from the Presidency. We can’t hand over our government to someone whose deepest, darkest secrets may be in the hands of our enemies.”
June 22, 2016: “10 days after Trump’s Reddit gets a big spike in members, less than 2 weeks post-Jr.’s meeting, Trump Tower -Alfa Bank pings begin. Seth Abramson
June 12, 2016 “72 hours after Don Jr met with a Russian agent at Trump Tower, the top Trump fan-site had its largest-ever membership spike by FAR.” Seth Abramson
Alleged hacker held in Prague at center of ‘intense’ US-Russia tug of war The Guardian
Yevgeniy Nikulin faces extradition requests from both countries amid lingering disquiet over Moscow’s alleged interference in the US presidential election

“An alleged computer hacker being held in the Czech Republic is at the centre of an international legal tussle between the United States and Russia amid lingering disquiet over Moscow’s alleged interference in the recent US presidential election.
Yevgeniy Nikulin, 29, faces extradition requests from both countries after being detained by Czech police on an Interpol arrest warrant issued by US authorities.
Nikulin, a Russian citizen, was arrested in a restaurant in Prague on 5 October shortly after arriving in the city during a holiday with his girlfriend.
He faces a maximum 30 years in prison and up to $1m in fines if convicted on charges including computer intrusion, aggravated identity theft, conspiracy, damaging computers and trafficking in illegal access devices.
There is no acknowledged link between Nikulin’s alleged offences and the hacking of Hillary Clinton’s presidential campaign, but his arrest came just three days before the Obama administration formally accused Russia of stealing emails from the Democratic National Committee and disclosing them through WikiLeaks.
Formspring, one of the sites he allegedly hacked, was the platform used for sexting by Anthony Weiner, the former New York mayoral candidate and husband of Huma Abedin, Clinton’s closest aide. The discovery of emails linked to Clinton on Weiner’s laptop damaged her campaign in its final two weeks after the FBI director, James Comey, revealed their existence.
Meanwhile, Russia has responded to the American extradition request against Nikulin by tabling one of its own, demanding that he be returned to face allegations dating back to 2009 that he hacked another person’s bank account and stole 111,000 roubles (£1,465).
“He was never formally accused at that time. I think the reason is that he was recruited [by the Russian security services],” said Ondrej Kundra, political editor with the Czech weekly magazine Respekt, which has reported that the Russian services offer alleged offenders immunity from prosecution in exchange for collaboration.

“There’s intense lobbying in this case. People from the US and Russian side are talking to the Czech authorities because both really want Nikulin in their countries.”
Fuelling speculation is the existence of sealed US court documents, tabled six days after the original indictment against Nikulin on 20 October but whose contents have not been revealed.
“A number of documents were filed under seal, which means you cannot talk about them,” a US justice department spokesman told the Guardian.
Adam Kopecky, Nikulin’s Czech lawyer, said his client denied both the US and Russian charges and suggested he had become a political pawn. “My client and myself think it’s a political affair,” Kopecky said.
“Given the international situation, when one superpower accuses a citizen of the other of hacking their computers and then the other superpower accuses the same citizen of another crime, it’s kind of strange.”
Nikulin has suffered health problems since his arrest, his lawyer said.
Kopecky lodged an official complaint after prison authorities put his client under high-level supervision that included monitoring his communications with the lawyer.
“He is unhappy about being detained for a long time in a foreign country and about the accusations against him. He wants to return to Russia – but as a free man,” Kopecky said.
The case is currently in the hands of Prague’s chief prosecutor, who is expected to issue a decision on the twin extradition requests at the end of this month or early in February, a spokeswoman for the city’s municipal court said.
Russia’s embassy in Prague declined to comment but cited a previous foreign ministry statement in which a spokeswoman compared the affair to other incidents and called it “another proof that the US law enforcement agencies are hunting for Russian citizens across the world”.
A 32-year-old Russian computer programmer named only as Lisov was arrested by Spanish police at Barcelona airport this month on another US arrest warrant. Police in Spain said he was suspected of leading a financial fraud network and having designed and used software to steal account details from banks and individuals.
Another Russian citizen, Roman Valerevich Seleznev, was convicted last year of 38 hacking-related charges by a US court after he was arrested and extradited from Guam in 2014. Russia said Seleznev’s arrest amounted to “kidnapping”.” The Guardian
Young Russian denies she aided election hackers: ‘I never work with douchebags’ The Guardian

Her company was a surprise inclusion on the US sanctions list released last week, alongside top officers in Russia’s GRU military intelligence agency and two well-known criminal hackers. The company “provided the GRU with technical research and development”, according to the fact sheet released by the White House. No further details were given.
In addition to the sanctions, the US expelled 35 Russian diplomats from the country, and said it would take further, non-public measures in response.
After a week in which Russian interference in the election – apparently with the goal of helping Donald Trump to victory – has dominated the news agenda, Shevchenko has spoken out to decry the sanctions against her.
Shevchenko told the Guardian she was furious at her company’s inclusion on the list, and denied ever having knowingly worked for the Russian government. She communicated via encrypted email, from a location she said was “a wild countryside area a few hours away from Bangkok”.
In answers that were defiant, and occasionally abrasive, she decried the “insane level of hysteria around the entire ‘Russian hacking’ story”.
She suggested that the US authorities were guilty either of “a technically incompetent misinterpretation of the facts” or had been fooled by a “counterfeit in order to frame my company”. Those who could have had an interest in framing her could include competitors, US intelligence or Russian intelligence, with the goal of screening the real culprits, Shevchenko said.
“A young female hacker and her helpless company seems like a perfect pick for that goal. I don’t try to hide, I travel a lot, and am a friendly communicative person. And most importantly, I don’t have any big money, power or connections behind me to shrug off the blame. So really, it could be anyone.”
US intelligence believes the Democratic party’s servers were hacked by a group known alternatively as Fancy Bear, APT 29 or Sofacy, which they say was working for the GRU, Russia’s military intelligence. In the private sector, attribution directly to the GRU comes most clearly from US firm CrowdStrike, which is influential in US security circles. The US government believes the hacked emails were then leaked – possibly through an intermediary – to Julian Assange and WikiLeaks.
Russian authorities are known to offer a mixture of carrot and stick to engage prominent hackers in work for the state, and third-party contracting of state information security tasks is common in most countries. A number of Russian security experts declined to comment, citing the sensitivity of the subject.
“Pretty much everyone in the community has done some work for their government at some point,” said Dave Aitel, who runs Immunity, a US software security company. He described Shevchenko as “extremely well known in the information security community”.
Shevchenko described herself as “a typical introverted computer geek” who is largely self taught. She declined to say how old she was, deeming it an “impolite question”, saying instead: “If you really need a number then go ahead and make it up based on my photographs”.

She said she dropped out of three different universities, as she was passionate about learning but did not enjoy the structure of a university course. Around 2004, she joined Kaspersky Lab, a high-profile Russian cybersecurity firm.
Shevchenko specialises in finding so-called “zero-days”, previously undisclosed software bugs that could leave companies vulnerable. “We have not only searched for bugs but exploited them, but only with the customer’s sanction,” she said. She said she never hired anyone she knew to have a criminal background for her companies.
Shevchenko said she had been approached repeatedly by people she believed to be from the Russian government. She insisted, however, that she had always rejected the advances. She said she had not been threatened or intimidated as a result.
A 2014 profile of Shevchenko in Russian Forbes magazine noted that she worked with DialogNauka, a Russian company that listed among its clients the Russian ministry of defence and parts of the security services. Questioned by the Guardian, she insisted that none of her own work for DialogNauka “was even remotely possible to use as a nation-state attacks supply”.
Shevchenko said she had turned down plenty of offers of work on ideological grounds: “I never work with douchebags. I only work with honest and open people that I feel good about.” Asked directly if she had ever worked on a government contract in any capacity, she answered “not that I know of”.
Shevchenko said ZOR was closed more than a year ago, because it was difficult and expensive to do the requisite public relations work required to drum up business. She now works as a “one-man army”, she said.
Many analysts have said it seems very likely that Russian state actors are behind Fancy Bear, but concede that the publicly released evidence does not include a smoking gun.
Brian Bartholomew, of Kaspersky Lab’s US office in Massachusetts, said the biggest clue was an in-house piece of software called XAgent, which he had never seen elsewhere.
“Assange said it could have been a 14-year-old hacker – if you look at the collective operations of this group, there’s no way a 14-year-old has this much money, time and effort to conduct all of these operations together,” he said.
Of the entities on the sanctions list, including Shevchenko’s company, Bartholomew said: “There’s probably a good reason that those names were put in the document.”
Aitel said he had no doubt Russian intelligence was behind the hack and said authorities would certainly use third-party contractors for operations, but he added that it was problematic to sanction individuals without releasing evidence. “No matter what she did technically, she’s not a policy maker. It doesn’t make much sense to sanction individuals on the basis that ‘we know something secret so we’re going to sanction you’.”
Only Shevchenko’s company – rather than Shevchenko personally – is on the US treasury’s list of specially designated nationals (SDNs), which are subject to an asset freeze in any dealings with US persons or the US financial system.
“If she starts a new company, then that company is clean, but a lot of people might not want to do business with her if they do their due diligence and find that she’s one step removed from an SDN,” said Louis Rothberg, an expert in export control with the international law firm Morgan Lewis & Bockius.
Shevchenko said she assumes it is “not possible” for her to travel to the US now, and she does not particularly want to.
“I am now de facto blocked from the world’s major information security market,” Shevchenko said.
On the other hand, she allowed, there was apparently a certain cachet in being named as someone who hacked a US election. “I have received a number of employment, business partnership or collaboration offers” in the days since the sanctions list was released, she said. ” The Guardian
“Je suIS IS,” read another. But the second message was a lie.
According to security researchers, the culprit was a Russian hacking team long believed by cybersecurity analysts in and outside the US government to be working for the country’s largest intelligence agency, GRU. Fascinated researchers have given it a variety of names: APT 28, Strontium, the Sofacy Group, and Fancy Bear.
Last week, WikiLeaks distributed 20,000 emails from the Democratic National Committee (DNC) obtained after Fancy Bear and another hacking team believed to be tied to a competing Russian intelligence service, known as Cozy Bear, breached the DNC’s internal network. Cozy Bear is believed to have entered the network a year before and waited quietly, gathering information and cataloging emails. Fancy Bear came later. WikiLeaks’ consistent position is not to discuss its source and to push back against suggestions that it gained the data from either Bear.
The Bears have three important things in common: expensive digital tools, suggesting state sponsorship; an interest in pursuing sensitive, embarrassing or strategically significant information, rather than financially beneficial data; and a choice of targets that align with Russian political objectives. Both Bears infiltrated the DNC: Cozy beginning in summer 2015, Fancy in April this year.
Senior US government sources are not primarily concerned with WikiLeaks’ role in the affair. Their alarm, shared by cybersecurity researchers, is that a Russian hacking operation they consider tied to the Russian government has taken a step toward attacking an element of the US political apparatus.
“Targeting a political campaign, trying to find out everything you can about the next leader of the free world, is fair game for intelligence services, as much as we hate it. That’s a valid intelligence target,” said Toni Gidwani, a former Defense Intelligence Agency (DIA) analyst who is now chief researcher for the cybersecurity firm ThreatConnect.
“Dumping this much information and [leaving] very much the sense that there’s more to come, we have to ask different questions about what the Russian objectives are and what they think is going to happen.”
Neither the DIA nor the FBI, which has an investigation open into the DNC hack, would address whether it assesses Fancy Bear to be an instrument of the Russian intelligence apparatus. Some administration officials are unsure whether the US would make a public accusation against the Russians. But, one said, the administration is coming to the conclusion that Moscow is responsible for the hack, despite foreign minister Sergey Lavrov’s protestations.
The blurred distinction between espionage and attack online has outpaced thinking about deterrence and reprisal, meaning both an intrusion and an accusation carries the risk of escalating beyond tolerable levels. One senior official notes that the executive branch tends to be “highly circumspect” about pointing a finger at Russia.
That escalation risk is heightened because of the mystery surrounding the DNC hack. If it is the Russians, the change represented by making stolen data public raises questions on questions: did something go wrong? Or did Russia mean to push the envelope with its principal geopolitical rival? Or could cybersecurity analysts be wrong, and the ties between the Bears and Russian government objectives be less substantial than they believe?
“The implications of those assessments have some pretty stark recommendations for our leadership, so it is only appropriate to go back and double-check,” said Gidwani. “But by the same token, if everything else looks completely implausible, what’s left is probably what’s happening.”
Patterns of infiltration
Cozy Bear has a sense of humor.
According to Kaspersky, one of its most effective methods of intrusion involved hiding a virus inside a email message that played a Career Builder ad from Super Bowl XL. The ad showed a human office worker trying to tell his colleagues, who are all chimpanzees, to stop wrecking the office.
“These videos are quickly passed around offices with delight while systems are infected in the background silently,” wrote despondent Kaspersky researchers.
A key characteristic of Bear attacks – and high-quality attacks from many seasoned intruders – appears to be its adroit disguise of malicious files. In another operation, a group Kaspersky believes to be Cozy Bear sent “highly relevant and well-crafted content” – such as PDFs about Ukraine possibly joining Nato – to people who would open them and find them interesting without becoming suspicious. Sophisticated users who would spot a “YovTube.com” address or an amateurish website inviting them to type in a login might eagerly open an official-seeming white paper.
Fancy Bear has its own signatures: its identifiable suite of tools has, since 2007 or perhaps even 2004, been updated with the frequency of a software company, according to security firm FireEye. FireEye gave all the tools names – Sourface, Chopstick and Eviltoss, among others – and described them as demonstrating “formal coding practices indicative of methodical, diligent programmers”.
Rather than send its malware broadly, a pattern used by hackers who hope a fraction of their recipients will click on a dubious link, Fancy Bear sends them to specific users, in a pattern Gidwani said indicates reconnaissance on its targets. Microsoft reported that Fancy Bear finds unsuspecting users both by sifting through social media and other online data for associations with its target – say, a LinkedIn page that lists the DNC as an employer – and also by meticulously cataloging the data it has stolen in previous hacks.
“They customize their attack to thrive in that environment,” said Gidwani. “Somebody who could do that has resources, has time and a test environment to try all the stuff out to make sure they’ve got the right package they’re going to deploy. Those are hallmarks of nation-state operations. Criminals are going to hit a million people in the hope that they get a hundred.”
Fancy Bear also favors infected files, in which it usually hides Sourface, the program that creeps on to a target computer and downloads malware allowing that computer to be controlled remotely. A list of “lure” emails compiled by FireEye includes a file named “military cooperation.doc”, a Georgian-language IT document for the ministry of internal affairs, and an offer of work to a journalist from the editor of a fictitious division at Reason magazine.
Cooper Quintin, a security researcher for digital rights activists the Electronic Frontier Foundation, said that when his organization was spoofed by Fancy Bear last year, it was part of an attack on a different target. “Some friends at Google” tipped him off that someone was squatting on electronicfrontierfoundation.org, a domain the company didn’t own then, though now it links to Quintin’s post on the event.
Quintin notes that Fancy Bear benefits greatly from general ignorance about digital security: high-quality spearphishing works often, and zero-days are pricey. “Why run [a zero-day] when people still open email attachments?” Quintin asked. “It’s usually associated with criminals but it works for nation-states, too.”
Attribution is tricky, Quintin said – often, patterns only become clear after a team has been completely exposed. But there are ways to make educated guesses.
Even if a user doesn’t fall for the login page trap, Fancy Bear can glean information from the click: the user’s IP address and location, his or her browser type and version, and the target computer’s operating system.
Metadata associated with the malicious code used by Fancy Bear suggests a point of origin. Its language settings are Russian, and the malware FireEye found was overwhelmingly built during the workday in Moscow and St Petersburg.
Information worth more than money
Once either group acquires the credentials it needs for its current operation, it uses flaws in popular software to secretly send data back to its own networks without its targets’ knowledge. These flaws, known as zero-day exploits, are critical tools of any hacking organization, from thieves to spy agencies – by definition, they’re difficult for administrators to defend against. The NSA is fond of them.
Zero-day exploits are not for novice hackers. They are difficult to design and keep stable. Purchasing them on the black market is very expensive. Misused, they can collapse forever when an exploited company notices them and fixes the weakness in its software.
Used effectively, zero-day exploits can be used to steal huge amounts of money. That objective has been a hallmark of other sophisticated state-sponsored hackers. China’s famous Unit 61398 tends to steal intellectual property and information beneficial to economic activity.
But Fancy Bear and Cozy Bear don’t do that.
FireEye notes that Fancy Bear wants to exfiltrate sensitive data by camping out on a network undetected for long periods of time – a network controlled or associated with a political, military, diplomatic, activist or journalistic entity. The team acquires “intelligence that would only be useful to a government”, the firm said. The targets chosen by the Bears suggest the government who would primarily find that intelligence useful is Russia.
Famously, when the Russian military attacked Georgia in 2008, its ground assault was presaged by overloading the servers used by the president, the foreign ministry and the parliament. “Georgia in a lot of ways was one of the real opening shots in how we see Russia using cyber as an instrument of national power, fully integrated with their national objectives,” Gidwani said.
Other targets show Bear attacks moving westward – much as Russia’s intervention in Syria, its first beyond its historical frontiers in a generation, followed years of unanswered military boldness against its neighbors.
Also in 2013, Kaspersky noticed a group it called MiniDuke – now believed to be Cozy Bear, as well – sneaking into targets in Hungary, Luxembourg and Belgium. Other targets include prime Russian multilateral adversaries like Nato and the Office of Security Cooperation in Europe. And in July 2015, an infiltration into an email system used by the US military’s joint chiefs of staff led military officials to suspect Russian culpability; CrowdStrike points a finger at Cozy Bear. Around the same time, Cozy Bear made its way into the DNC’s network.
Doubt as an objective
While the FBI investigates the DNC hack, politics has taken the place of digital forensics.
Democrats have already begun to seize upon the hack to imply, as yet without evidence, that the Russians executed the attack to benefit GOP nominee Donald Trump, who has openly praised the Russian president, Vladimir Putin, something that sets him apart from any other major Republican figure in recent memory.
Cozy Bear infiltrated the DNC months before Trump surprised the political world by winning the nomination; nevertheless, the senior Democrats on the congressional intelligence committees on Wednesday called for an extraordinary declassification of intelligence assessments about the hack. The White House said it would “carefully review” the request, but the National Security Council spokesman, Ned Price, said that the just-launched FBI inquiry into the hack “will necessarily limit what we will be able to say”.
A major question at issue in the inquiry is whether the Russians, should they be culpable, intended the DNC infiltration and subsequent publication to influence the outcome of the 2016 election. ThreatConnect’s Gidwani suspects that Russia may not have had so sophisticated a plan.
“Part of me feels like that might be a more aggressive reading of what’s happening. If their objective is primarily to be a distraction, to sow confusion, to sow doubt, that doesn’t require the creation of this airtight persona,” she said, referencing the hacker persona Guccifer2.0, who claims to have passed the documents to WikiLeaks and whose authenticity has come under serious doubt.
Gidwani continued: “It allows you a lot more wiggle room and ability to fudge around the edges to create that type of effect. It’s an incredibly important question, whether Russia is trying to push the outcome of the election one way or the other. But I think we may not be sufficiently considering that that might not be the primary outcome they’re seeking.
“And that shouldn’t necessarily be cause for relief. Trying to sow this much doubt and discord is also very troubling. These types of actions, what we’ve seen thus far, they had been limited to eastern Europe, Georgia, Ukraine in the 2014 election. Moscow no longer sees the same line, if you will, between that near-abroad and the US.” The Guardian
Hospitals Gain Control After Ransom Hack, More Attacks May Come
“Ransom Hackers Who Hit Hospitals Dealt Setback; May Return,” by Bloomberg’s Jordan Robertson: “The cyber-attack that spread rapidly around the globe was stifled when a security researcher disabled a key mechanism used by the worm to spread, but experts said the hackers were likely to return as many computers remain at risk. Hackers can still gain easy access to personal computers that lack a security update issued in March by Microsoft Corp. to fix the vulnerability in its Windows operating system. … More than 75,000 computers in 99 countries were compromised in Friday’s attack, with a heavy concentration of infections in Russia and Ukraine.”
Russia has actual spy college, wherein people get trained in a variety of legitimate careers and then placed in strategic companies and organizations for espionage. They acually employ hackers, as the investigations have shown.
THE DNC EMAIL HACK
Hacked from March 2015-June 2016
THE PODESTA EMAILS
Hacked in March 2016 and released October 2016
